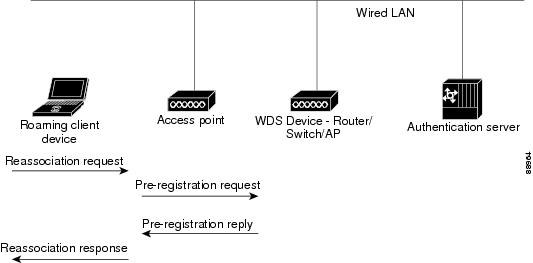
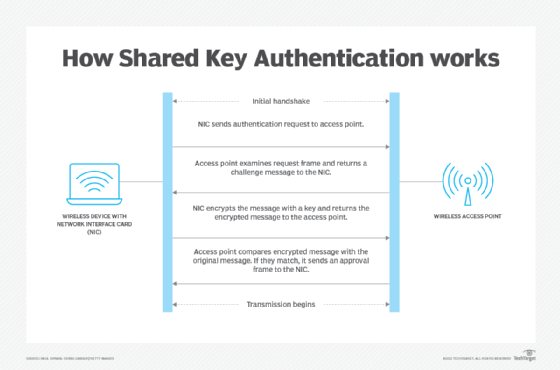
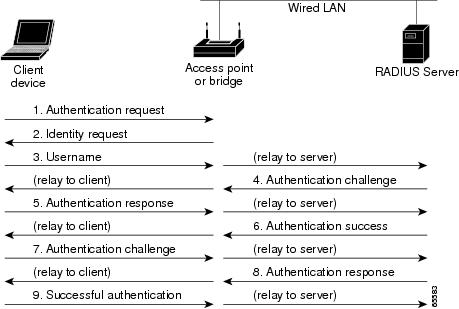
Pass-through Authenticator The authentication methods are facing to... | Download Scientific Diagram
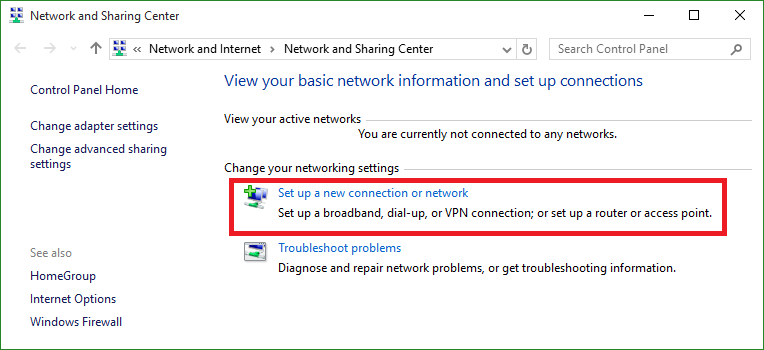
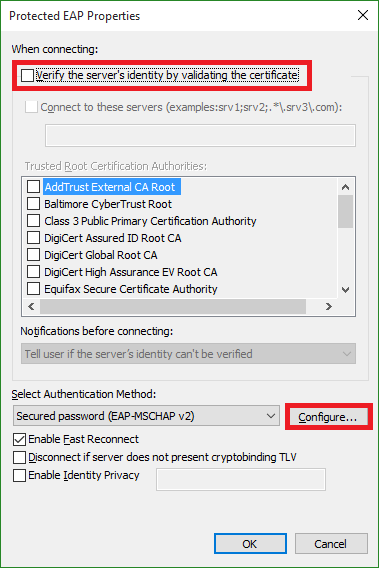
Wireless LAN Client Configuration Guide for Windows 10 Configuring 802.1X Authentication Client for Windows 10 1

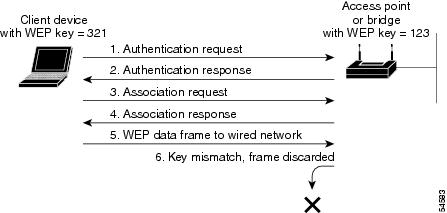
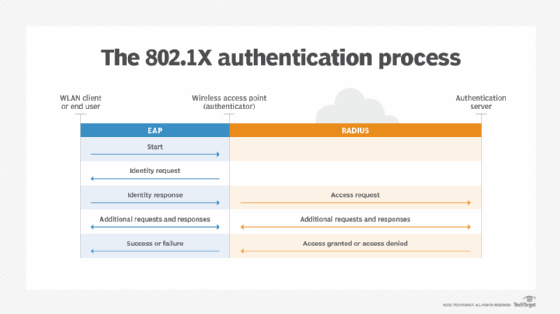
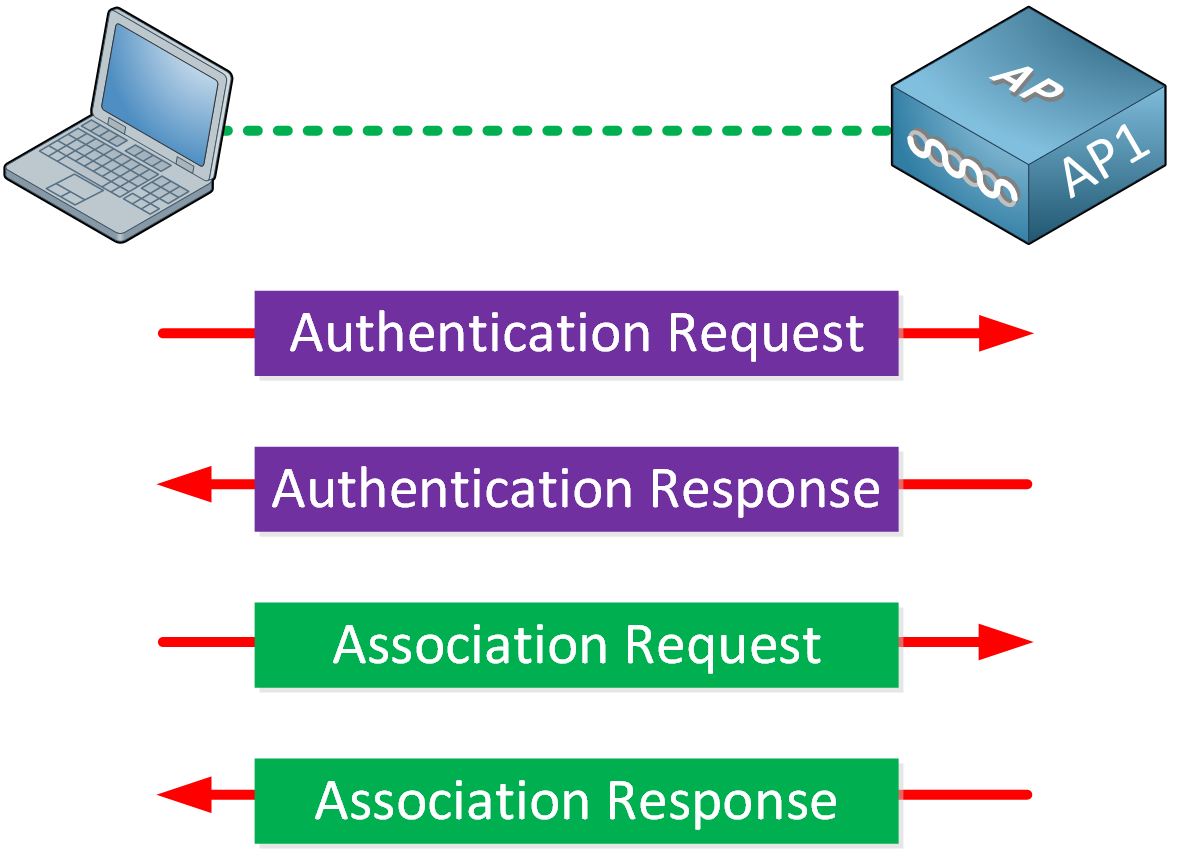
Wireless Authentication Methods - SY0-601 CompTIA Security+ : 3.4 - Professor Messer IT Certification Training Courses